According to The Hacker News , QakBot is a notorious Windows malware strain that is estimated to have compromised more than 700,000 computers globally and facilitates financial fraud as well as ransomware.
The US Department of Justice (DoJ) said the malware is being removed from victims' computers, preventing it from causing any further harm, and authorities have seized more than $8.6 million in illicit cryptocurrency.
The cross-border operation, which involved France, Germany, Latvia, Romania, the Netherlands, the UK and the US, with technical support from cybersecurity firm Zscaler, was the largest US-led crackdown on botnet infrastructure used by cybercriminals, although no arrests were announced.
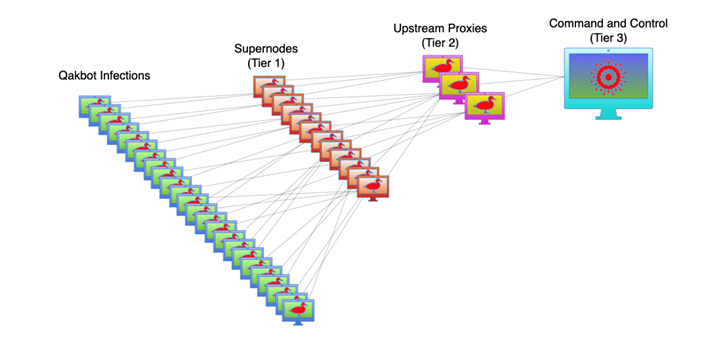
QakBot's botnet control model
QakBot, also known as QBot and Pinkslipbot, began operating as a banking trojan in 2007 before transitioning to serving as a distribution hub for malware on infected machines, including ransomware. Some of the ransomware from QakBot include Conti, ProLock, Egregor, REvil, MegaCortex, and Black Basta. QakBot’s operators are believed to have received around $58 million in ransom payments from victims between October 2021 and April 2023.
Often distributed via phishing emails, the modular malware is equipped with command-execution and information-gathering capabilities. QakBot has been continuously updated throughout its existence. The DoJ said that computers infected with the malware were part of a botnet, meaning the perpetrators could remotely control all of the infected computers in a coordinated manner.
According to court documents, the operation accessed QakBot infrastructure, which allowed it to redirect botnet traffic through FBI-controlled servers, with the ultimate goal of disabling the criminals’ supply chain. The servers instructed compromised computers to download an uninstaller, which was designed to remove machines from the QakBot botnet, effectively preventing the distribution of additional malware components.
QakBot has shown increased sophistication over time, quickly changing tactics to accommodate new security measures. After Microsoft disabled macros by default in all Office applications, the malware began using OneNote files as an infection vector earlier this year.
The sophistication and adaptability also lies in the weaponization of multiple file formats such as PDF, HTML, and ZIP in QakBot's attack chain. The majority of the malware's command and control servers are located in the US, UK, India, Canada, and France, while the backend infrastructure is believed to be located in Russia.
QakBot, like Emotet and IcedID, uses a three-tier server system to control and communicate with the malware installed on infected computers. The primary and secondary servers' primary purpose is to relay encrypted communications between infected computers and the third-tier server that controls the botnet.
As of mid-June 2023, 853 tier-1 servers have been identified in 63 countries, with tier-2 servers acting as proxies to mask the main control server. Data collected by Abuse.ch shows that all QakBot servers are now offline.
According to HP Wolf Security, QakBot was also one of the most active malware families in Q2 2023 with 18 attack chains and 56 campaigns. This shows the trend of criminal groups trying to quickly exploit vulnerabilities in network defenses for illegal profits.
Source link



![[Photo] Prime Minister Pham Minh Chinh chairs the conference to review the 2024-2025 school year and deploy tasks for the 2025-2026 school year.](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/8/22/2ca5ed79ce6a46a1ac7706a42cefafae)

![[Photo] President Luong Cuong attends special political-artistic television show "Golden Opportunity"](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/8/22/44ca13c28fa7476796f9aa3618ff74c4)
![[Photo] President Luong Cuong receives delegation of the Youth Committee of the Liberal Democratic Party of Japan](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/8/22/2632d7f5cf4f4a8e90ce5f5e1989194a)






























































































Comment (0)