LockBit 3.0 Ransomware Analysis Report Released
During the 3 weeks from March 24 to the first week of April this year, Vietnam's cyberspace recorded consecutive targeted attacks in the form of ransomware on large Vietnamese enterprises operating in important fields such as finance, securities, energy, telecommunications, etc. These attacks caused the systems of the enterprises to be suspended for a period of time, causing significant economic and reputational damage to the units whose systems were targeted by cybercriminal groups.
During the process of analyzing and investigating the causes and groups of subjects that have recently attacked the information systems of Vietnamese enterprises, the authorities found that these incidents were the 'products' of many different attack groups such as LockBit, BlackCat, Mallox... In particular, with the ransomware attack on the VNDIRECT system at 10:00 a.m. on March 24, which encrypted all data of enterprises in the top 3 of the Vietnamese stock market, the authorities identified the LockBit group with the LockBit 3.0 malware as being behind this incident.
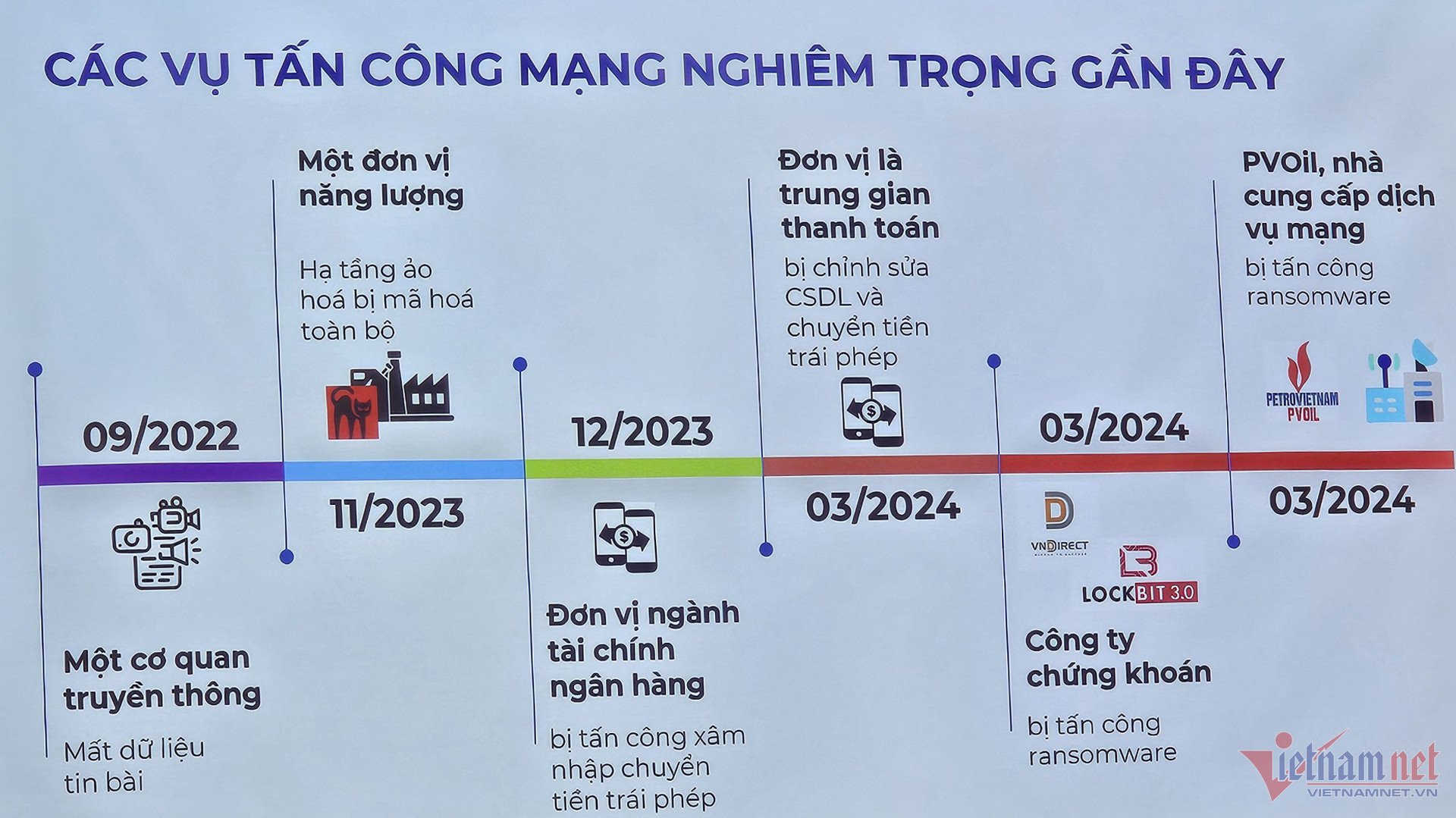
Worldwide , the LockBit group has launched many ransomware attacks targeting large businesses and organizations. For example, in 2023, in June and October respectively, this notorious ransomware group attacked Semiconductor Manufacturing Company TSMC (Taiwan, China) and Information Technology Products and Services Company CDW, with the amount of data ransom that the Lockbit group required businesses to pay up to 70 - 80 million USD.
With the desire to help agencies, organizations and businesses in Vietnam better understand the level of danger and how to prevent and minimize risks from ransomware attacks in general as well as attacks by the LockBit group, the National Cyber Security Monitoring Center - NCSC under the Department of Information Security (Ministry of Information and Communications) has just synthesized information sources on cyberspace and released the 'Analysis Report on ransomware LockBit 3.0'.
The world's most dangerous ransomware group
The new report conducted by NCSC focuses on providing 4 main contents, including: Information about the LockBit ransomware attack group; Active LockBit clusters; List of recorded cyber attack indicators related to LockBit 3.0; How to prevent and minimize risks from ransomware attacks.
Identifying LockBit as one of the most dangerous ransomware groups in the world, the NCSC report also said that since its first appearance in 2019, LockBit has carried out numerous attacks targeting businesses and organizations across various sectors. The group operates under a 'Ransomware-as-a-Service (RaaS)' model, allowing threat actors to deploy ransomware and share profits with those behind the service.

Notably, in September 2022, the source code of LockBit 3.0, including some of the names that could be used to develop this ransomware, was leaked by an individual named 'ali_qushji' on the X platform (formerly Twitter). The leak allowed experts to further analyze the LockBit 3.0 ransomware sample, but since then, threat actors have created a wave of new ransomware variants based on the source code of LockBit 3.0.
Along with analyzing the attack methods of active LockBit ransomware clusters such as TronBit, CriptomanGizmo or Tina Turnet, the NCSC report also provides units with a list of cyber attack indicators related to LockBit 3.0 that have been recorded. "We will continuously update IOC indicator information on the alert.khonggianmang.vn page of the national cyberspace portal," said an NCSC expert.
A particularly important part mentioned in the 'LockBit 3.0 Ransomware Analysis Report' is the content guiding agencies, organizations and businesses on how to prevent and minimize risks from ransomware attacks. Important notes to support units in Vietnam in preventing and responding to ransomware attacks have been mentioned by the Department of Information Security in the 'Handbook on some measures to prevent and minimize risks from ransomware attacks' released on April 6, and continue to be recommended for implementation by NCSC experts.

According to experts, ransomware attacks today often start from a security weakness of an agency or organization. Attackers penetrate the system, maintain presence, expand the scope of intrusion, control the organization's IT infrastructure and paralyze the system, with the aim of forcing real victim organizations to pay ransom if they want to recover encrypted data.
Sharing with VietNamNet reporters at the time the attack on the VNDIRECT system occurred 5 days ago, from the perspective of the unit participating in coordinating incident response support activities, a representative of the Department of Information Security commented: This incident is an important lesson to raise awareness of network safety and security of organizations and businesses in Vietnam.
Therefore, agencies, organizations, and businesses, especially those operating in important fields such as finance, banking, securities, energy, telecommunications, etc., need to urgently and proactively review and strengthen both the existing security systems and professional personnel, and at the same time develop incident response plans.
“Organizations need to strictly comply with the regulations, requirements, and guidelines on information security and network security that have been issued. This is the responsibility of each organization and enterprise to protect themselves and their customers from potential cyber attacks,” emphasized a representative of the Information Security Department.
| The LockBit ransomware was first known as ABCD after the encrypted file extension, and a few months later a variant of ABCD emerged with its current name, Lockbit. A year later, the group released an upgraded version, LockBit 2.0 (also known as LockBit Red), which included another integrated malware called StealBit for the purpose of stealing sensitive data. LockBit 3.0, also known as LockBit Black, is the latest version, released in 2022 with new features and enhanced evasion techniques. |

Why can PVOIL system recover quickly after ransomware attack?

Forming a security culture to increase defenses against ransomware attacks

Paying ransoms will encourage hackers to increase ransomware attacks
Source



![[Photo] President Luong Cuong receives delegation of the Youth Committee of the Liberal Democratic Party of Japan](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/8/22/2632d7f5cf4f4a8e90ce5f5e1989194a)
![[Photo] President Luong Cuong attends special political-artistic television show "Golden Opportunity"](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/8/22/44ca13c28fa7476796f9aa3618ff74c4)


![[Photo] Prime Minister Pham Minh Chinh chairs the conference to review the 2024-2025 school year and deploy tasks for the 2025-2026 school year.](https://vstatic.vietnam.vn/vietnam/resource/IMAGE/2025/8/22/2ca5ed79ce6a46a1ac7706a42cefafae)



























































































Comment (0)